%20(1).png)
Whether you are investigating an endpoint in your corporate environment or you are part of a criminal investigation, you need to investigate the USB device history of an endpoint. Knowing what USB devices were connected to the computer is the essential information and of great importance to a forensic examiner.
This feature is mostly provided by traditional desktop forensic solutions or specifically designed standalone solutions but with TACTICAL, you get the full forensic snapshot + USB storage history with one fast and simple solution.
Below you can find steps:
-
Once you execute TACTICAL on your machine on the main user interface you will see already selected evidence and artifact types. These by default selected evidence and artifacts are carefully chosen, so end users can get a forensic snapshot in less time and effort.
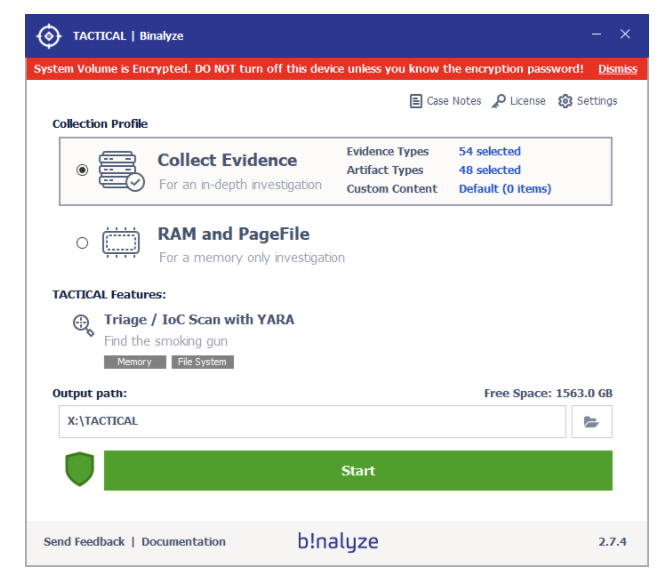
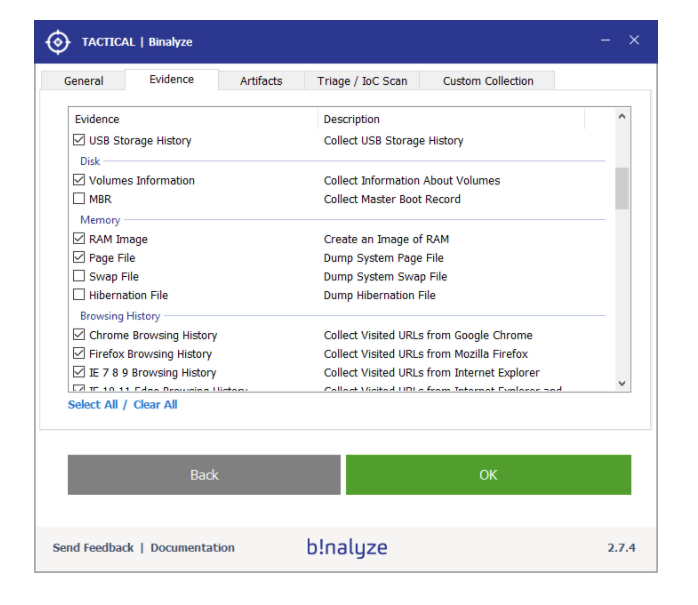
2. Click on the evidence types and you will notice that USB Storage History is already pre-selected. Click on “OK” and let’s start the evidence collection.
3. You will notice that the digital evidence acquisition is done in less than 10 minutes while processing 40 GB of data and 988 files.
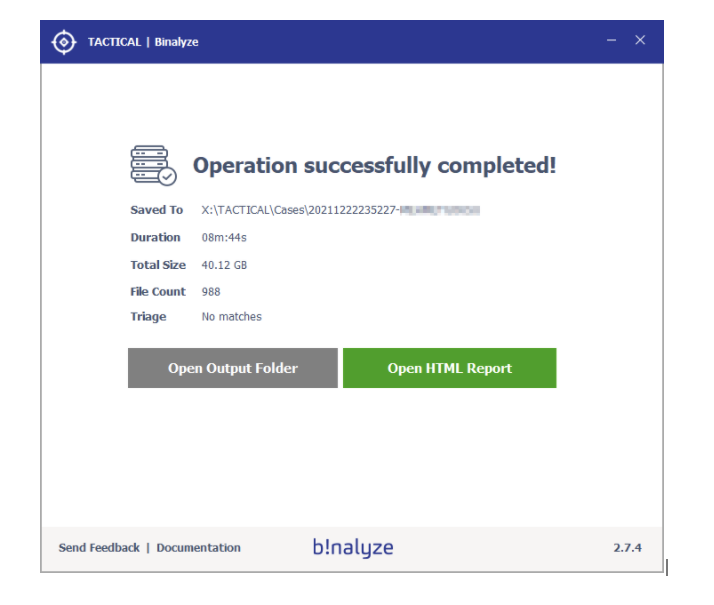
4. Once the evidence collection process is complete, open the HTML Report. In the report menu, you will find a list of collected evidence types containing parsed data. Clicking on any of the evidence types will display a table of parsed data. You can easily search, filter, view details, and bookmark items in these lists.
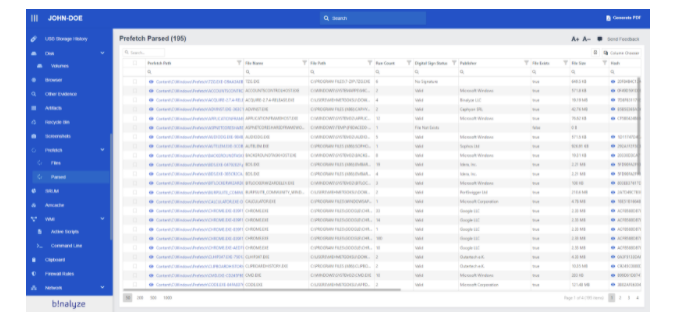
Also when you select the USB Storage History from a report you can easily see inserted USB drives with their extended information like Serial, First Install, Last Arrival, and Last Removal.
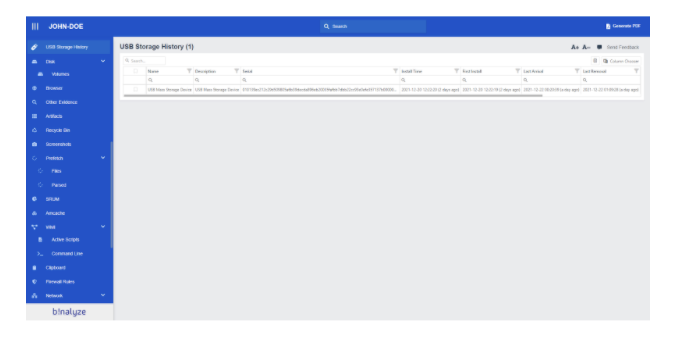
And that is all.
Using a traditional digital forensics approach it would take hours to reach this kind of comprehensive collection and report but with TACTICAL you can get a full forensic snapshot + USB device history in less than 10 minutes and with zero manual work.
Learn more about TACTICAL here.









