Welcome to our monthly product updates roundup! Here’s a rundown of the new features and solutions we released in the past month that you can now take advantage of.
AIR v1.8.0
In the past month we released a new version of AIR that includes the following new features:
-
Multiple organization support
-
Elevated security with Azure AD SSO and 2FA support
-
Network capture option to acquisition profile
-
Wazuh integration support
-
Docker-based installation support
You can download it now from www.binalyze.com/air.
Elevated security with Azure AD SSO and 2FA support
With the newest AIR version when Single Sign-On is enabled, users are not required to enter their application account credentials to connect to the AIR dashboard. Authentication is performed using the user’s Azure account details. In this way, SSO simplifies the sign-in process tremendously.
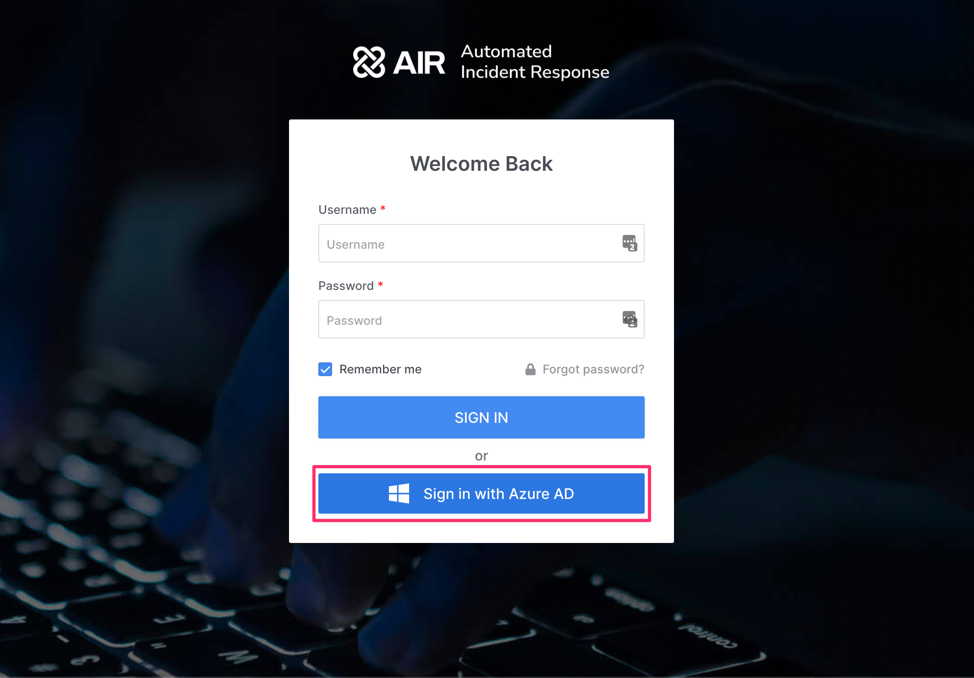
In case you don’t use Azure SSO for your secure login system, with this AIR version we are introducing 2FA to improve security by asking users to provide additional authentication factors to their login. On this link, you can learn more on how to set up SSO and 2FA in AIR.
Additional SSO providers will be coming in future releases.
Network capture option to acquisition profile
With the release of Binalyze AIR v1.8.0, we are introducing network capture capabilities to the acquisition profiles so you can capture both Network Flow (TCP/UDP connections) and PCAP IP packet data directly within the AIR platform.
This upgrade brings significant advantages by further consolidating all your digital forensics activities into one solution and collaborative platform that delivers automation to save you time, reduce your costs and increase efficiency. On this link, you can learn more about network capture and how to use it in AIR.
Wazuh integration support
Having Binalyze AIR integrated into your SIEM allows you to react in real-time by starting a forensic acquisition on the endpoint whenever there is a suspicious activity detected by the SIEM. By creating a simple rule, AIR acquires evidence and stores it in the chosen evidence repositories.
Wazuh is one of the most popular open-source SIEM in the world. For that reason, we decided to incorporate Wazuh integration out-of-box into this product release to make daily DFIR duties more manageable and efficient. Click here to learn more about Wazuh integration.
Docker-based installation support
With this version of AIR we shifted to Docker-based installation support. In this article, you can read all about how to migrate from v1.7.61 to v1.8.0.
If you don’t have AIR, you can get it on AIR product page.
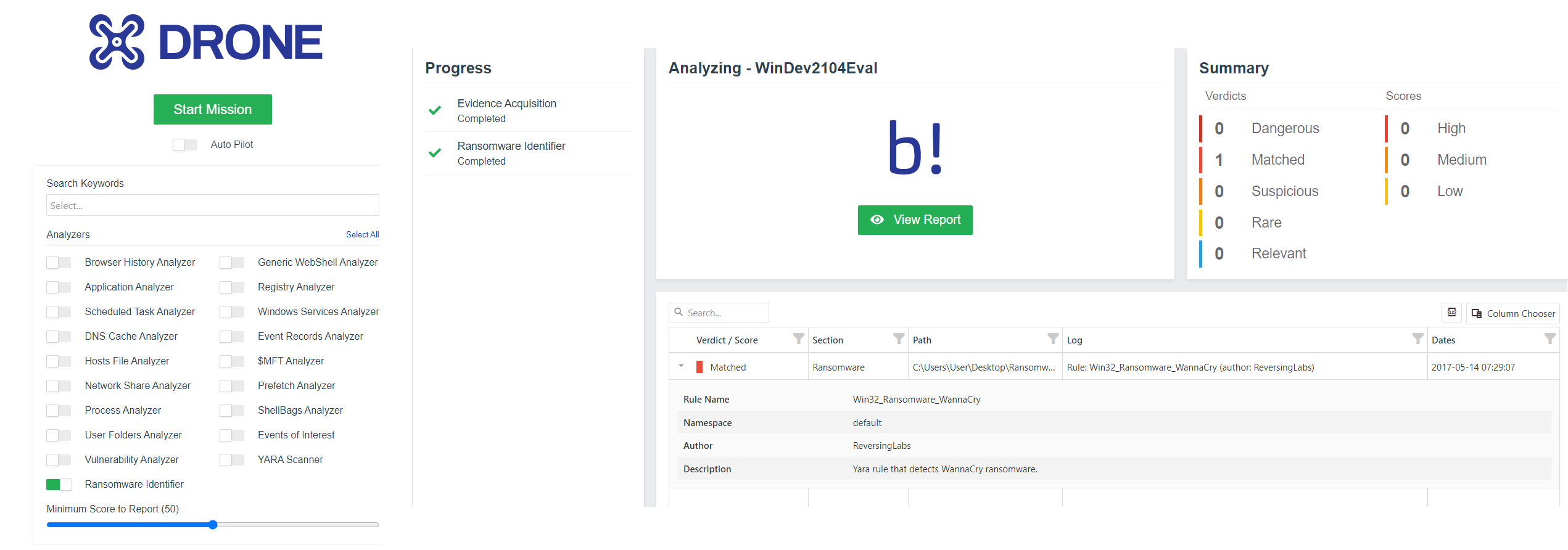
DRONE Release v1.6.0: YARA Scanner & Ransomware Identifier
DRONE v1.6.0 release highlights:
-
YARA Scanner
-
Ransomware Identifier
-
Sigma public repository synchronization
-
Pull YARA repositories from the config file
YARA Scanner & YARA repositories
Starting from this version, DRONE supports a generic YARA scanner. You can provide your own list of YARA rules as shown below and DRONE will automatically execute them.
As a linked feature to the YARA scanner, we have also added a new configuration section called YARA repositories that allows you to provide publicly available repository links (Github and Gitlab) into this section and sync it to DRONE. This will automatically add the provided YARA rules from the repository so you can always have up-to-date YARA rules throughout your investigation tasks.
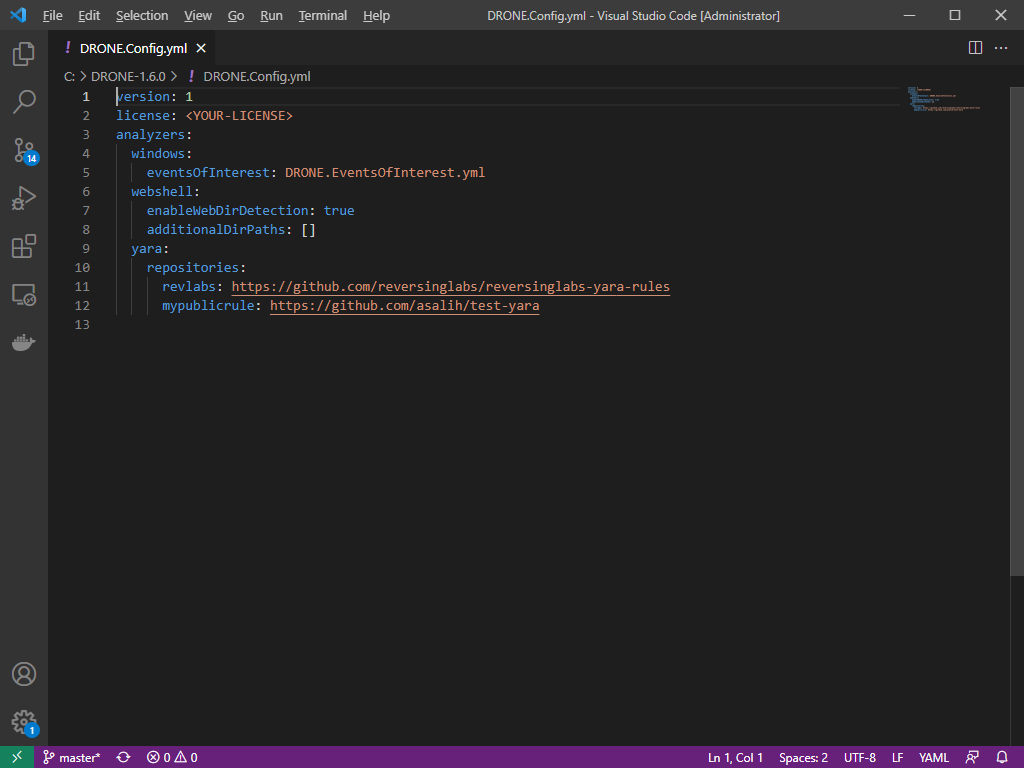
Ransomware Identifier
This new feature will scan your machines for ransomware and detect any traces of it. We are using reversing labs’ ransomware rules to scan machine process paths, prefetch paths, user root folder, and its subdirectories, to speed up the detection process and increase efficiency by scanning the locations where ransomware resides.
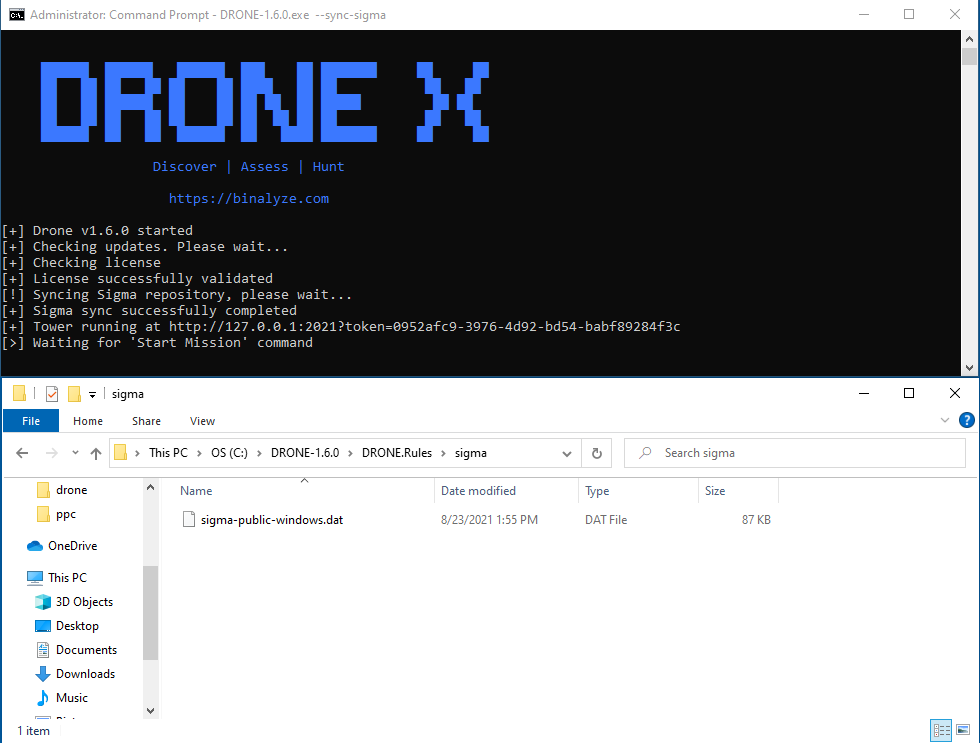
Sigma public repository synchronization
Running Sigma rules on a live machine is a key benefit of DRONE. Now, this feature allows you to stay always up to date with the latest public Sigma repositories. If there are any new rules available, instead of adding them manually, with this version just use the sync feature and DRONE will automatically update.
How to get the new version?
If you would like to try the DRONE new version, please visit www.binalyze.com/drone.
TACTICAL 2.7.0
Whether you are investigating an endpoint in your corporate environment or you are part of a criminal investigation, you will have needed to investigate the USB device history of an endpoint. Knowing what USB devices were connected to the computer is essential information and of great importance to a forensic examiner.
This feature is mostly provided by traditional desktop forensic solutions or specifically designed standalone solutions but in our case, with the newest version of TACTICAL, it is combined into the product so you get the full forensic image + USB storage history with one solution.
Added support for MFT as CSV collection from all drives
With this version of TACTICAL, you can collect all files from the MFT including the deleted ones. Previously TACTICAL was only collecting MFT from the system volume but with this version, it is collecting from all attached volumes. Besides enumerating deleted files in this version we further enrich the MFT by adding support for alternate data streams which is a feature of NTFS that may be abused by hackers to hide additional data that is not visible to the end-user. It is a great place to hide suspicious data and with this version, TACTICAL collects those fields as well.
Added support for evidence exclusion at the command line parameters
If you want to acquire evidence and you want to use the full acquisition profile that contains more than 60 evidence types but in this acquisition profile you don’t want to collect RAM you can do that by simply using the evidence exclusion at the command line parameters.
Below you can find an example: