1 min read


It has been quite a long time since the last time we updated you with what’s new on Binalyze. The reason for that is it was a very busy period full of new features, updates, and even a new product! Now it is time to share the news with you.
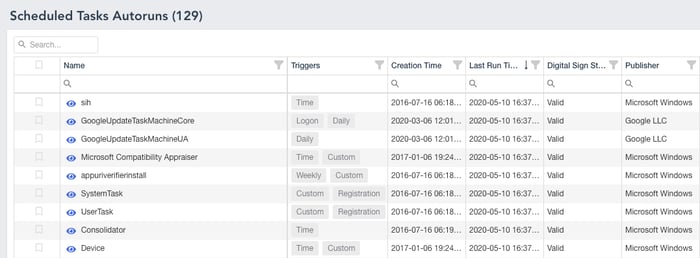
As we all know, investigating a PC is getting harder each and every day due to the increasing complexity of Cyber Attacks. Even though we have designed IREC to be the most complete evidence collector in the market there was still a missing piece: Autostart Locations. As of Windows 10, there are more than 200 registry and file system locations that could be abused by malware and attackers! It means, on a regular PC you will have approximately 1000 entries in total that have the potential of executing malicious code on each system restart. The good news is, IREC v2 lists all of these in an intuitive way with all the information you need such as Digital Signature of the file in question, MAC times for each entry, last write time of the registry key, and the hash of the file!
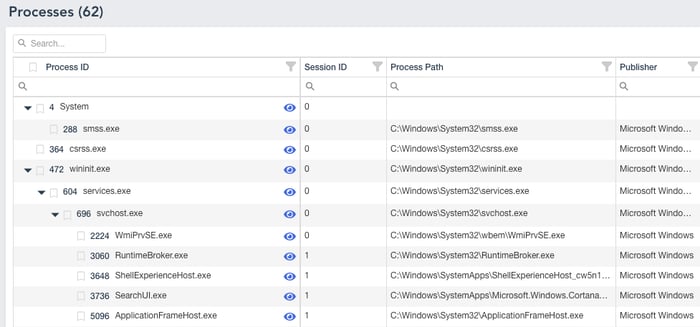
Version 2 comes with an all-new easy to use process viewer in which you can filter, search, and show the details of each process alongside important information such as TCP Connections, Modules, and other details.
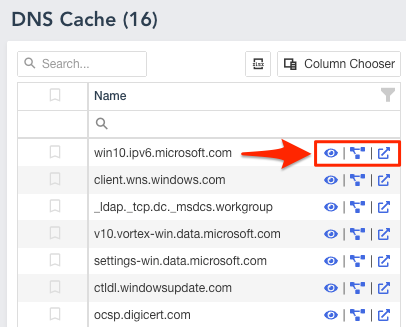
The new report lets you view Virus Total results and relations for each URL and IP Address with a single click.
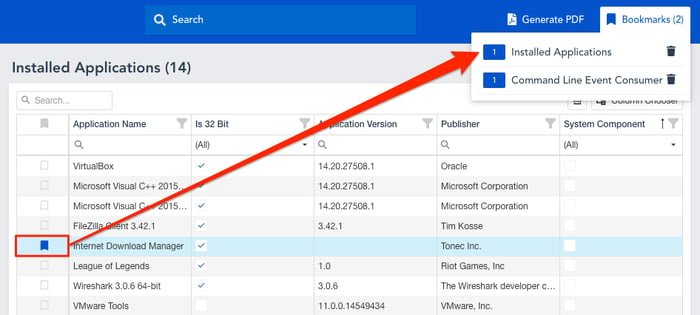
Wouldn’t it be great to bookmark the pieces of evidence either for further investigation or reporting purposes? That’s why we have added an easy bookmarking feature which will persist in the browser’s local storage. So you won’t lose your bookmarks even when you close the browser.
This is just a quick summary of what we have added to the latest version so far. For the full list you can visit IREC page.