Acquisitions in Minutes
Evidence acquisition is completed in under 10 minutes (average) instead of hours or days using legacy tools.
Built on our proprietary IREC engine, collecting digital forensic evidence from any endpoint on your network is just a few clicks on the AIR management console, and is completed in minutes.
Evidence acquisition is completed in under 10 minutes (average) instead of hours or days using legacy tools.
Once deployed across your network, endpoint tasks and actions can be run concurrently and at scale.
Acquired evidence can be compressed to save storage resources and encrypted to AES-256 military-grade encryption standards.
Evidence can be stored on the local machine, an attached removable drive, a network location, an SFTP server, SMB share or Cloud repository on Amazon or Azure.
AIR’s unique features ensure acquired evidence is timestamped and ransomware shielded to maintain forensic integrity.
Leverage the power of digital forensics proactively by scheduling evidence acquisition and triggering tasks from other security systems.
Over 350 different evidence types, parsed and presented in a single report. AIR’s case report is a self-contained HTML/JSON file that can be easily shared between analysts.
You can find the full list of Evidence Types here.
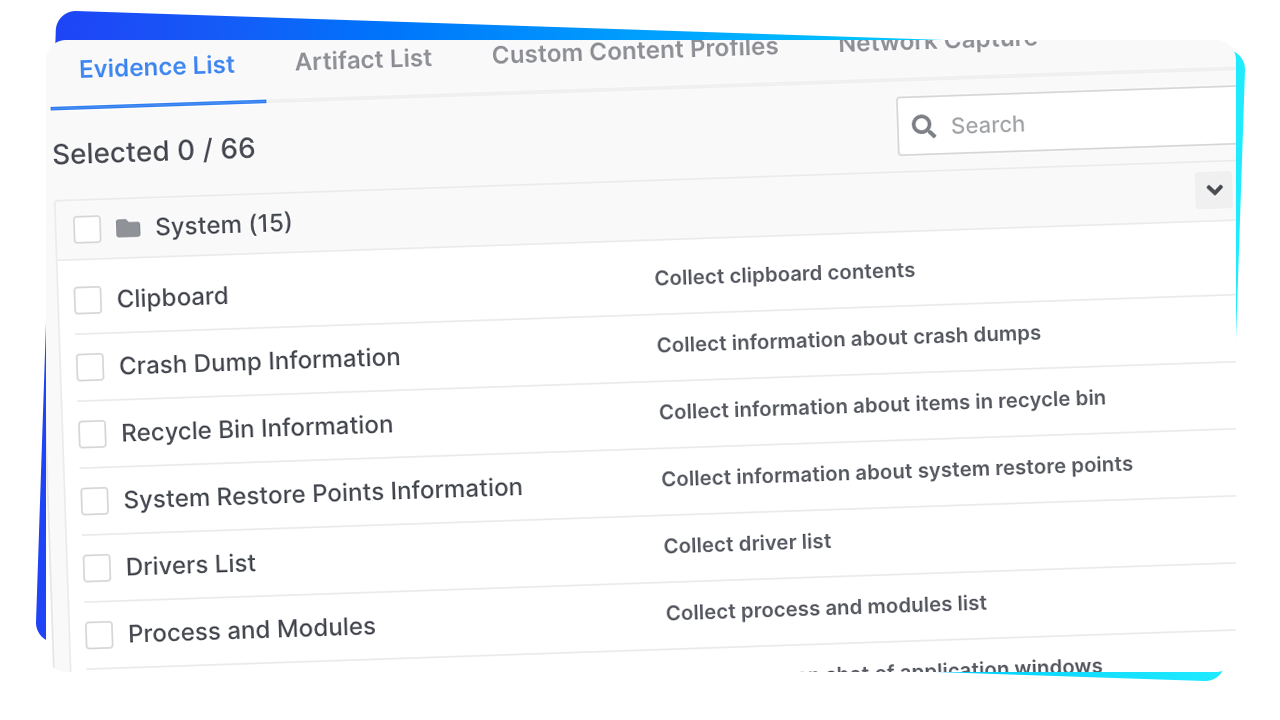
We collect more over 214 different types of system evidence in the following categories.
Disk Evidence
Memory Evidence
Browser Evidence
NTFS Evidence
Registry Evidence
Network Evidence
Event Logs Evidence
WMI Evidence
Process Execution Evidence
Miscellaneous Evidence
SSH Evidence
Users Evidence
File System Evidence
Configuration Evidence
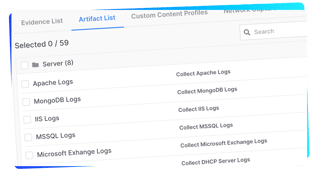
We collect over 138 different system artifacts in the following categories.
Server Artifacts
Microsoft App Artifacts
Communications Artifacts
Social Artifacts
Productivity Artifacts
Utility Artifacts
Developer Tools Artifacts
Cloud Artifacts
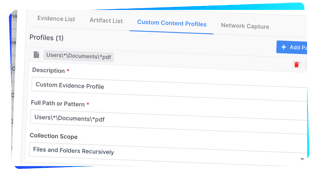
In addition to the 350+ evidence types collected, custom content profiles (path/pattern based) can be defined for specific evidence requirements.
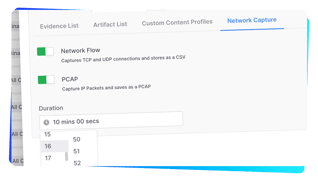
With AIR you can also capture network traffic at the endpoint level.
Network Flow captures the TCP and UDP connections.
PCAP captures the individual network IP packets for detailed network forensics.