.png)
Cybersecurity breaches have become increasingly common in recent years, with a growing number of employees within organizations falling victim to hackers and cybercriminals.
Digital Forensics and Incident Response (DFIR) experts are often called upon to investigate and mitigate the damage caused by these breaches. In 2022, the United States saw a number of significant DFIR breaches, each with its own unique characteristics and consequences.
In this blog post, we’ll take a look back at the five biggest DFIR breaches that occurred in the US in 2022.
By examining these high-profile cases, we can see just how many different sectors in the US remain vulnerable to attack and gain a better understanding of the evolving threat landscape and the importance of having a proactive platform like AIR at the heart of your SOC and cyber resilience efforts.
Colonial Pipeline
In May 2022, Colonial Pipeline, one of the largest fuel pipeline operators in the United States, suffered a ransomware attack that caused widespread disruption and fuel shortages in several states. The attackers were able to encrypt Colonial Pipeline's systems and demand a ransom of $4.4 million in Bitcoin.
The attack resulted in Colonial Pipeline shutting down its entire pipeline system for several days, leading to fuel shortages and panic buying in some areas. The attack highlighted the vulnerability of critical infrastructure in the energy sector to cyber threats and raised concerns about the potential for similar attacks in the future.
JBS
JBS is one of the world's largest meat processing companies, with operations in several countries. In June 2022, the company suffered a ransomware attack that disrupted its operations in several countries, including the United States, Canada, and Australia.
The attack resulted in the shutdown of several JBS plants, leading to meat shortages in some areas. The attackers demanded a ransom of $22.5 million in exchange for the decryption key.
The attack highlighted the vulnerability of the global food supply chain to cyber threats and raised concerns about the potential impact of similar attacks on critical infrastructure.
T-Mobile
T-Mobile is one of the largest mobile network operators in the United States, with over 100 million customers. In August 2022, the company suffered a data breach that compromised the personal information of over 50 million customers.
The attackers were able to access T-Mobile's customer data, including names, addresses, phone numbers, and social security numbers. The breach resulted in T-Mobile offering free credit monitoring to affected customers and faced criticism for its data security practices.
The T-Mobile breach shows the risk associated when repeated attacks, from external and internal threat actors, are not quickly identified and remediated. Resulting in a failure to adequately safeguard customer data.
Microsoft Exchange Server
In March 2022, various versions of Microsoft Exchange Server (2013, 2016, and 2019), a popular email server used by many businesses, suffered a vulnerability that allowed attackers to gain access to sensitive data. The vulnerability, dubbed ProxyShell, allowed attackers to execute code on vulnerable systems and gain access to emails, contacts, and other sensitive information.
The vulnerability was actively exploited by attackers, and it is estimated that over 30,000 organizations were affected worldwide. The attack shined a light on the importance of regular software updates and patching to prevent vulnerabilities from being actively and maliciously exploited.
The University of California, San Francisco (UCSF)
In July 2022, the University of California, San Francisco (UCSF) suffered a data breach that compromised the personal information of over 12,000 students, faculty, and staff. The breach was caused by a phishing attack that allowed attackers to gain access to UCSF's systems and steal sensitive data.
The attackers were able to access personal information, including names, social security numbers, and bank account information. The breach resulted in UCSF offering credit monitoring to affected individuals and caused an outcry on social media, with criticism focusing on the lack of data security practices.
The UCSF breach shows why it’s so important to have strong cybersecurity measures in place, including the need for better user training and general awareness, to prevent such phishing attacks from reoccurring in the future.
Time for a DFIRent approach
The above examples were high profile but by no means isolated cases. The reality is that, despite significant investment in blocking and monitoring solutions, a cyber breach is inevitable. The need for fast, scalable, and automated investigation and incident response capability will continue to grow.
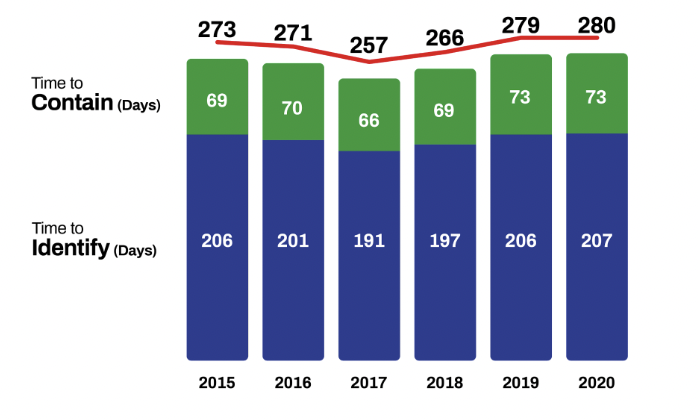
We see evidence for this in the static dwell time over recent years. A relative lack of investment in post-alert investigation capability (compared to blocking and monitoring) means that when there is a breach, it still takes around around 280 days to identify and contain.
Cyber threats will only continue to increase and evolve. Addressing them effectively will require a multi-layered approach that includes: better and more frequent employee cybersecurity education, timely software patching routines, and having highly skilled cyber security practitioners.
These professionals need to be armed with the right solutions that provide them with insights into the most vulnerable parts of their organizations. It’s clear that prevention measures alone are not enough.
They need the ability to proactively identify and hunt threats based on indicators of compromise (IOC) and tactics, techniques, and procedures (TTP) used by threat actors. It's about moving quickly and efficiently to handle threats before they can walk away with sensitive information, this is key. This is why we built AIR, the fastest and most comprehensive DFIR platform on the planet.
To find out more about AIR and how it can improve your DFIR capabilities and help maintain a more resilient cyber security posture - why not sign up for a free 14-day trial?
Simply click the link below to start your trial today.










