1 min read


3 weeks ago, one of the biggest breaches happened where FireEye uncovered a malicious campaign that gained access to victims via trojanized updates to Orion, SolarWinds’ IT monitoring and management software. Being aware of the nationwide damages this breach will produce, Binalyze released an initiative where we decided to give support to SUNBURST damaged entities by releasing a version of Binalyze AIR with the codename SUNBURST that will enable anyone to identify their exposure to the attack and pinpoint their network vulnerability in under an hour.
This version is FREE of charge for 15-days and 25,000 endpoints.
Binalyze is the fastest evidence collection, triage, and IR investigation platform that now also contains the YARA Rules for SUNBURST thanks to our colleagues at FireEye. In the below lines you will find instructions how to perform a triage with already set YARA rules for SUNBURST in less than an hour.
Now it is time to showcase how easy it is.
Select an endpoint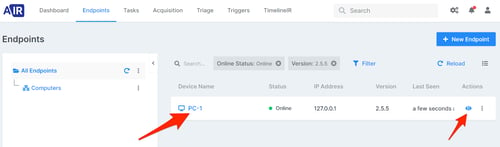
Click on “Triage” button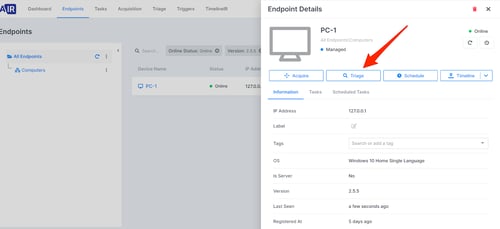
Select both SUNBURST YARA rules and click on “Save”.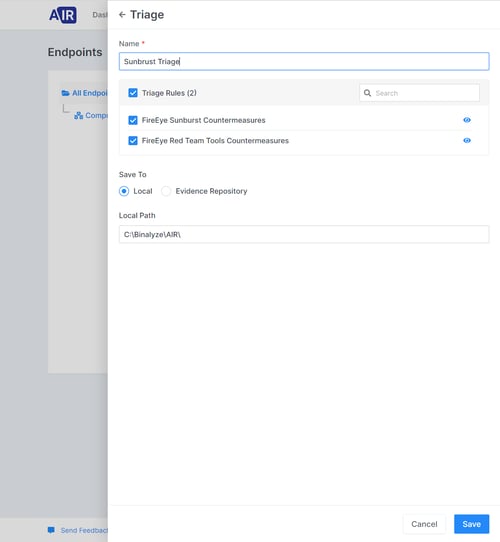
Triage is now in processing.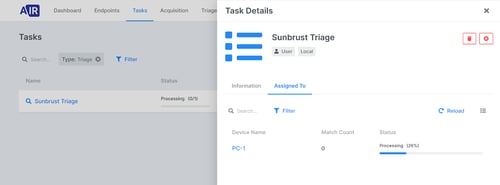
As said it is done in less than an hour or to be exact in 34 minutes.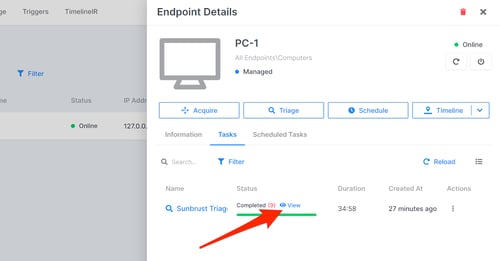
To see full view of the investigation results click on “View”.