
Before we dive into how to use the Webshell Detection feature in DRONE here is a quick reminder on what a web shell malicious attack is capable of.
It got its name by its shell-like interface that powers up a web server to be remotely accessed, but the uniqueness of this malicious shell script lies in the fact that a web browser is used to interact with the attacked server.
A webshell itself doesn’t have the characteristics of an attack but is rather a post-exploitation signal since it is always used in the second step of an attack to maintain continuous access on an already compromised web application. The common functionality includes but is not limited to shell command execution (access to cmd/command line), code execution, database enumeration, and file management.
In this article, we would like to show you how you can easily detect web shells and protect your assets using Binalyze DRONE.
-
Visit www.binalyze.com/drone to download the latest DRONE version so you can proceed with malicious webshell detection
-
For the purpose of this article, we will create a fake scenario where we have an infected server. So, here it is – even though at this stage you think that your web server functions normally because the IIS doesn’t show anything suspicious, your web server has been compromised.
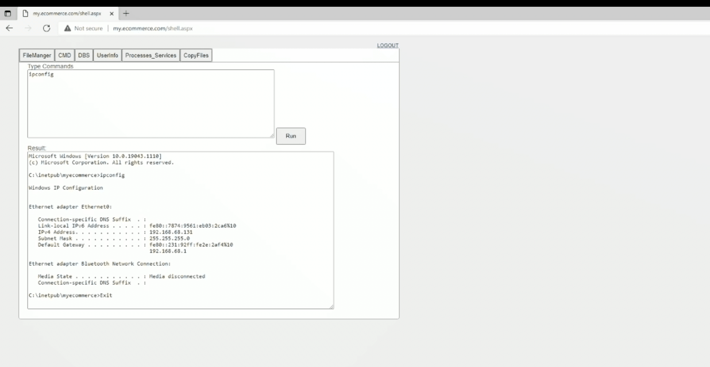
-
The only thing you need to do is open the DRONE application and “Start the mission”

In a couple of minutes, DRONE will find the malicious script and stop it from running
Here is where the story ends. At Binalyze we like to keep malicious story tales short and with a happy ending because in this way we know that the compromise has been blocked on time without additional incidents. When you have an incident in your organization’s network, to be effective, your response must quickly provide you with actionable information.
Binalyze has developed the ideal solution for this scenario. Even though the WebShell detection feature is an important feature in cybersecurity solutions this is just a small part of what DRONE is capable of. It is built for organizations that need to perform agile and efficient digital forensics investigations and compromise assessment remotely. It helps companies take back control over their incident response management by providing fast and accurate analysis for thousands of endpoints in a fully automated way.
You can use DRONE for:
-
Fully remote endpoint assessment
-
Ultra-fast Early Case Assessments
-
Automated Compromise Assessments
-
Rapid keyword searching of forensic evidence
-
Anomaly Detection on endpoint forensic data
-
Support for Sigma rules
-
Decreasing preliminary analysis time to minutes
-
Supporting analysts with less experience to make informed decisions










