
A couple of weeks ago, we released our new DRONE solution, which is set to transform remote digital forensics investigation by giving you the capability to quickly understand your network by acquiring and analyzing data across all endpoints in minutes.
So far, the feedback has been overwhelmingly positive, including some great qualitative feedback. Today we are releasing v1.3.0 which incorporates some of this feedback as well as some new features and enhancements from our roadmap.
So here we are with the release highlights:
-
Events of interest/ Watchlist
-
Syslog enhancements
-
Headless CLI mode
-
Sigma rules attributions
How to get the new version?
If you already have DRONE 1.2.0, just execute the product, and it will automatically download the new version to use the new feature set right away.
If you would like to try DRONE for the first time, please visit www.binalyze.com/drone.
Let’s dive into the new feature set.
Events of interest/ Watchlist
Starting from this version, you can provide a list of events for your investigation, and DRONE will automatically enumerate them in the provided time frame.
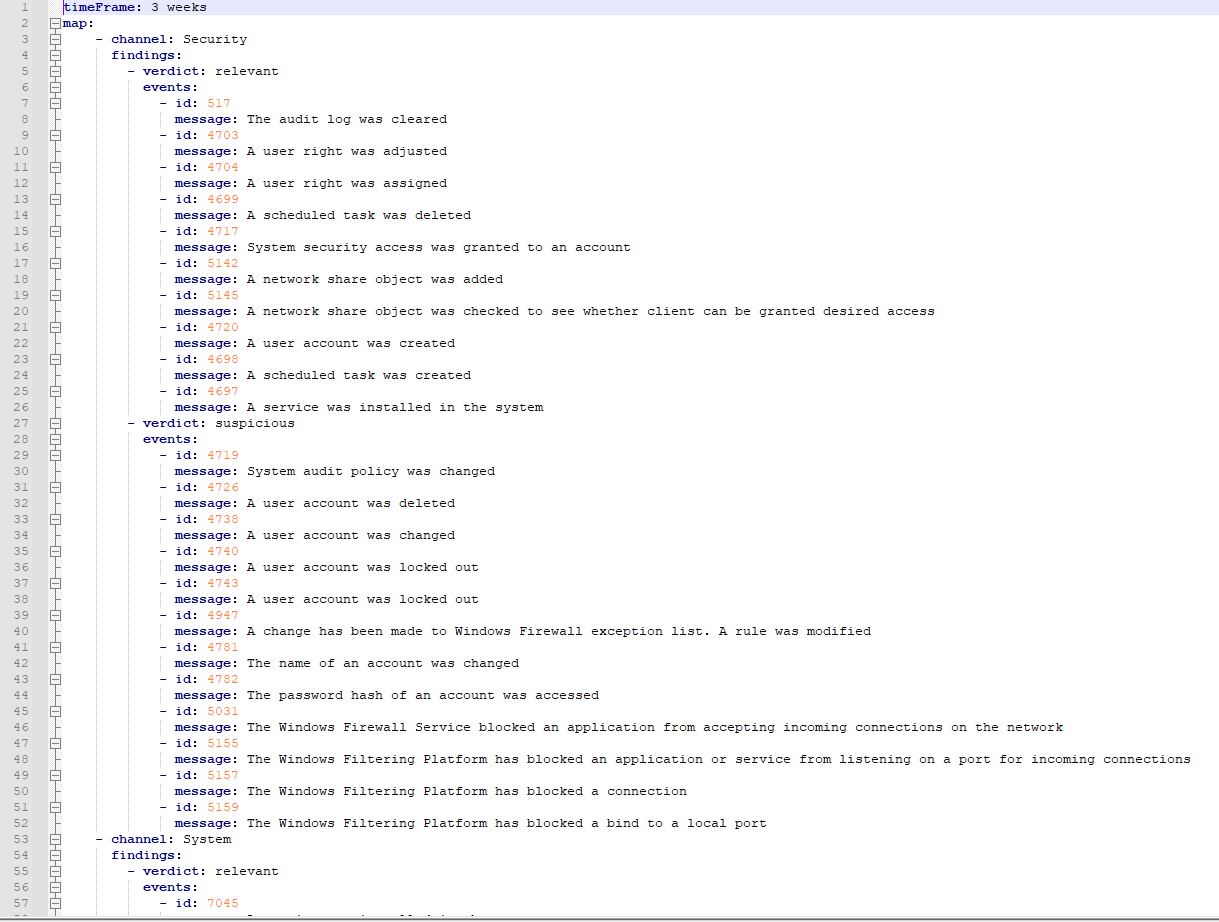 Now you can have your watchlist of events that you want to prioritize when you investigate a case. The supported time units are day, week, month, and year.
Now you can have your watchlist of events that you want to prioritize when you investigate a case. The supported time units are day, week, month, and year.
With this feature, you can:
-
Provide your list of events
-
Customize the events
-
Forget manual work because DRONE will automate this process by highlighting and labeling events at the same time.
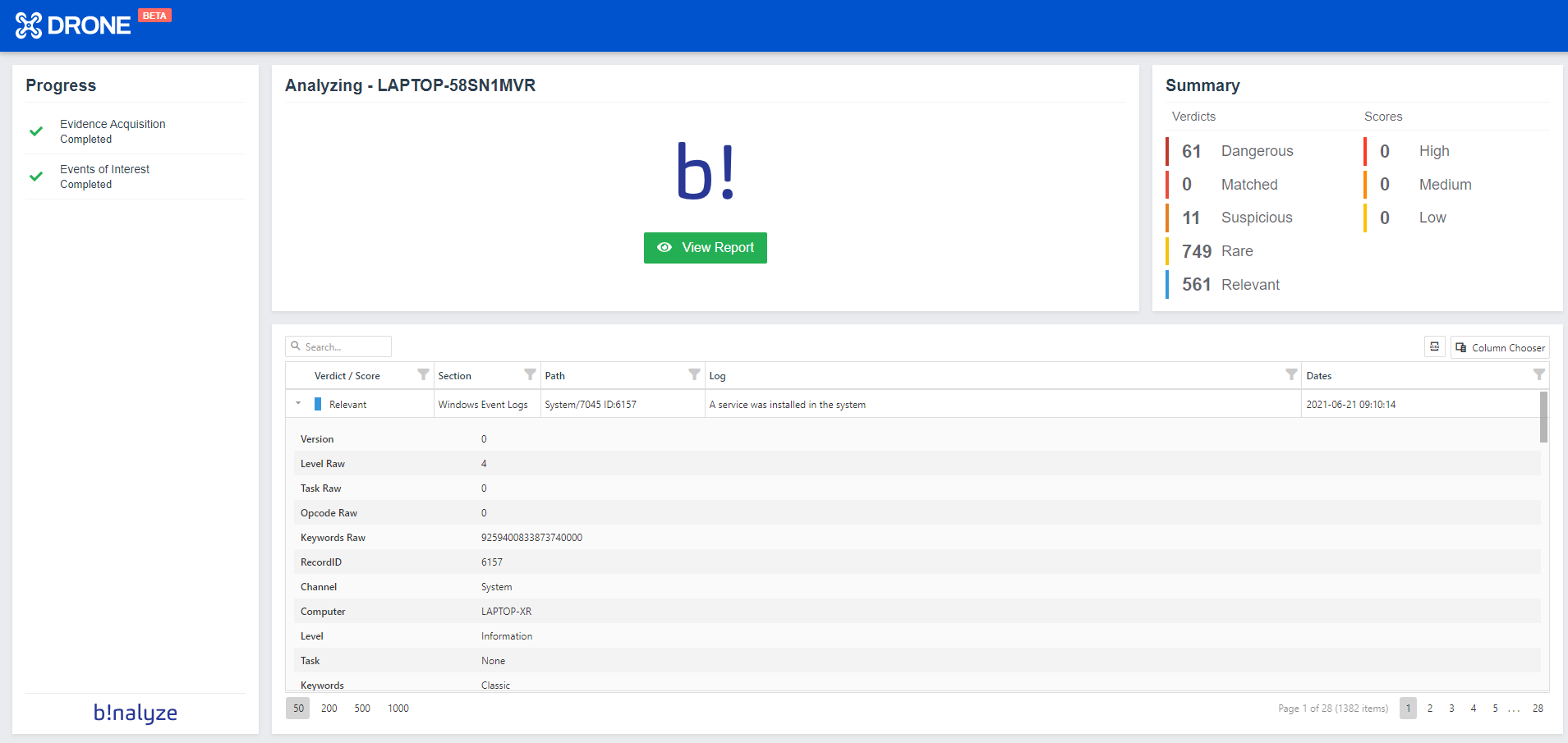
Syslog enhancements
With this version, you can submit all your findings to your Syslog server when you run DRONE from the command line. This automates your investigation process even more by giving you the possibility to run DRONE remotely, integrate it with your Syslog server and collect all the findings in one central location.
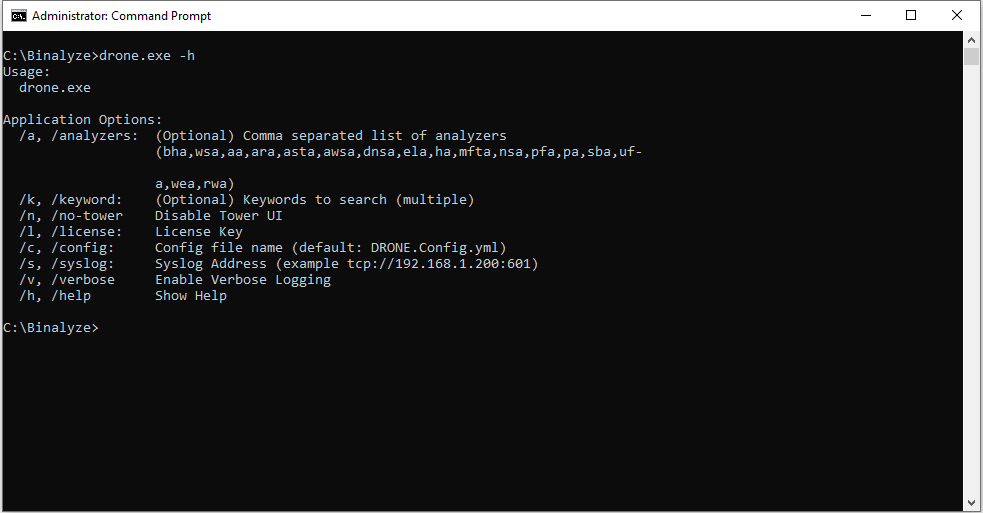
Headless CLI mode
With this version, you can entirely execute DRONE from the command line. By default, the outputs will be saved to a JSON file and the command line.
Sigma enhancements
From now on, we support Sigma repositories, publicly available Sigma rules embedded into DRONE.
Sigma is a community effort to write detections for IoC’s, and DRONE lets you scan these IoC’s on a live machine. Typically, these Sigma rules are designed to be executed or scanned on SIEM logs but with DRONE, you can find these IoC’s on a live machine.
With this version we have also added attributions, so the name of the rule creator will be visible in the detection details.










