
When a breach occurs one of the first questions the investigating team leader will want answered is, ‘how many of our assets could this potentially impact or has it already impacted?’
To best answer that question you’ll need to know what assets you have across your estate and do they have attributes that make them vulnerable to the current attack.
Enumeration and reconnaissance of assets is among the hardest and yet most important jobs in DFIR investigations. How do we know where to focus our efforts? For either 10 or 50,000 endpoints, prioritisation of a start point for the investigation is crucial to saving both time and money, as well as preserving usability across the network.
Key assets will be high on the list for investigators, so which ones out there are IIS Servers, Domain Controllers, Mail Servers? Is there a specific machine running an exploitable version of an application?
These are all crucial questions that need answering as quickly as possible.
Binalyze AIR has a feature called Auto Asset Tagging and this will answer all of these questions and much more.
Auto Asset Tagging lets you automatically tag your assets based on conditions such as the existence of a file or directory, or the existence of a running process.
Users can also easily add layers of ‘AND/OR’ conditions with other environment variables including Hostname, IP Address, Subnet and even more with the extremely powerful and customizable osquery functionality.
With the assets tagged it’s a very quick and simple process to identify and select all of the assets in your organisation by their tags for immediate further investigation.
Let's take a look at what comes ‘out-of-the-box’ with the AIR platform and then investigate how we can design and use our own Auto Asset Tags.
If the correct conditions are present the following tags will be applied to your asset listings in AIR as soon as you deploy agents to your endpoints:
-
Apache
-
Redis
-
Mysql
-
Rabbitmq
-
Docker
-
Kubernetes
-
Domain Controller
-
IIS Web Server
-
Web Server
-
Mail Server
-
MSSQL Server
When we look at the conditions set for the tagging of an Apache Server, we can see that the AIR agent will be looking at 5 conditions, all independent of each other as the OR switch is active. So, if any one of these conditions exist the Apache Tag will be applied to the endpoint.
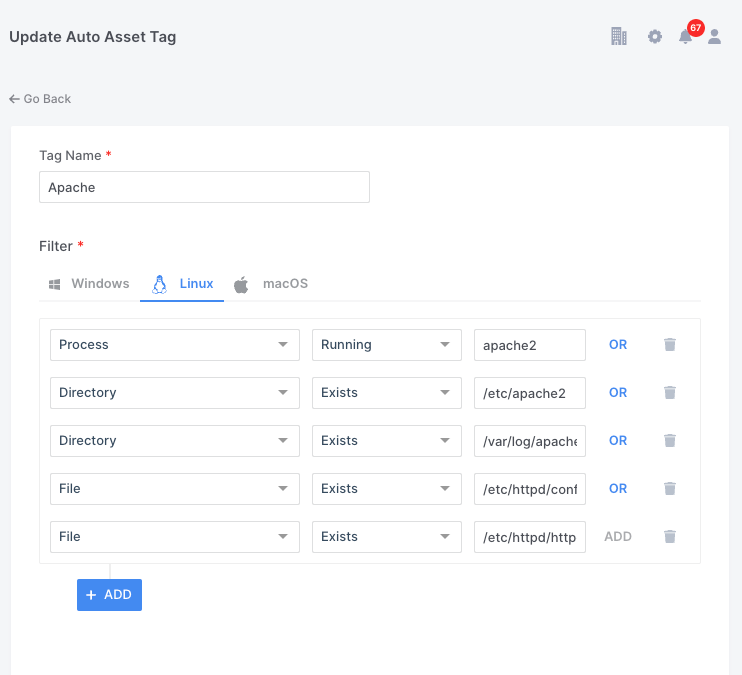
It is possible for a user to create, edit and delete the parameters shown below, but only if they have permission to do so.
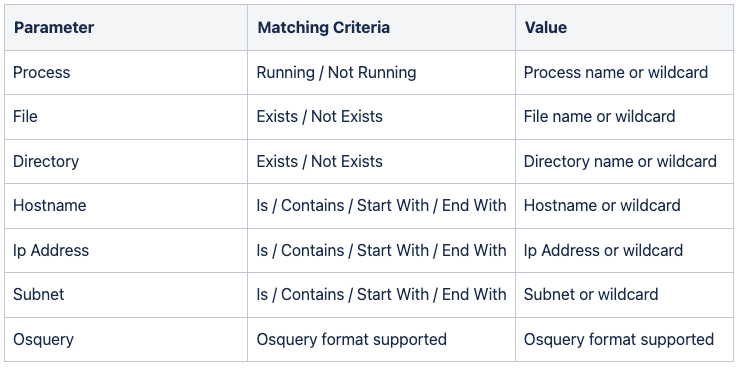
AIR has very granular permissions control over Users and Roles, and within Roles there are currently 106 individually configurable privileges. Six of these allow Global Administrators to determine what users can do within the Auto Asset Tagging feature alone.
Auto Asset Tagging for investigations
Auto Asset Tagging can be a very simple, fast and effective way to explore your endpoints. And, identify them immediately to you with either a single tag or multiple.
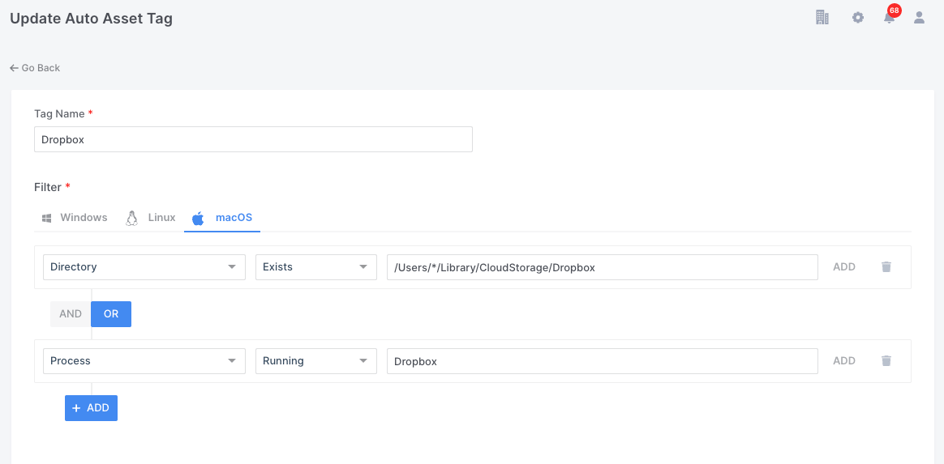
Imagine you discover that some of your employees had installed Dropbox on their devices. Perhaps this is against your company policy and you needed to establish how many or where these users were located, was it a trend in a particular office or region?
A simple Auto Asset Tag could be generated (as in the example below) and run across your entire estate within seconds and within a minute or two all of the connected devices with Dropbox installed will be identified to you with a ‘Dropbox’ Tag.
Once the Auto Asset Tag is generated it can be run ‘globally’ from the Settings - Auto Asset Tagging window:
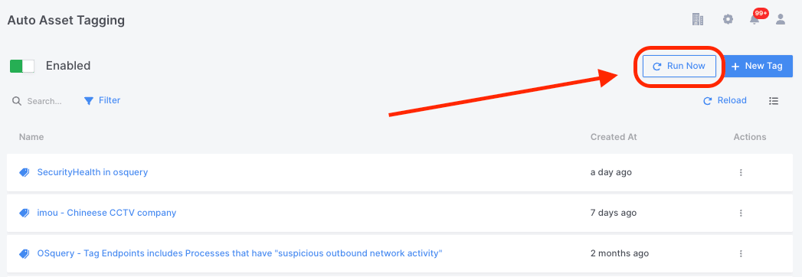
It can also be ‘re-run’ on individual assets from the refresh arrow found alongside individual endpoints as shown below:
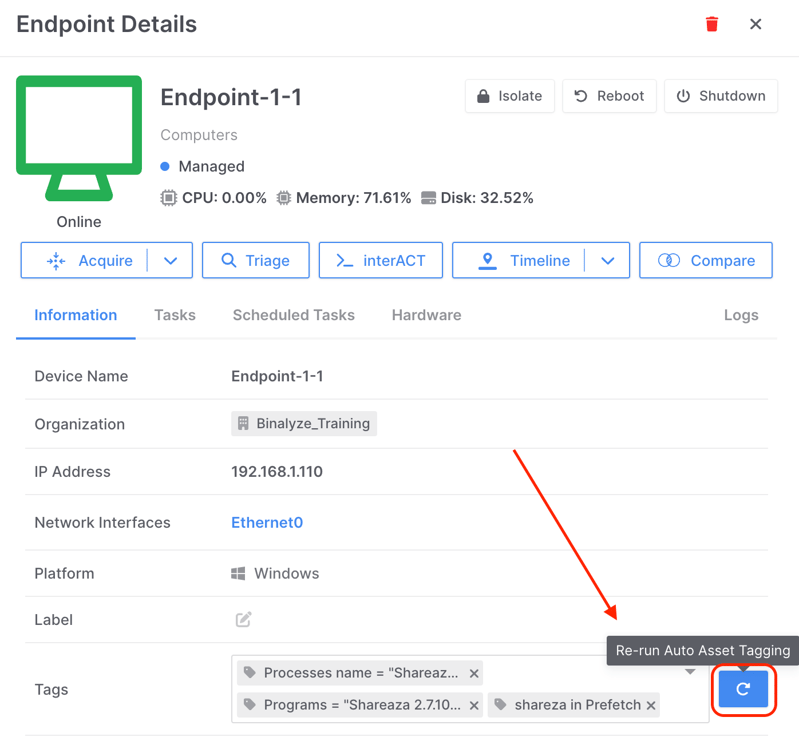
This simple methodology is exploited by users and has developed further as a ‘threat hunting’ technique.
For example, during a recent investigation of mine, DRONE, the super powerful, post acquisition analyzer built into AIR, identified that as a result of clicking on a malicious web link embedded in an email, a file called ‘trunk_3801543.zip’ was being placed in the users download folder. This file actually contained the Mimikatz binaries which the attacker was later able to execute on the targeted devices.
There are of course many other ways to investigate this discovery with AIR, such as triaging all of our endpoints for the hash value of the ‘bad file’, but a very quick and simple tactic could be to use Auto Asset Tagging as shown in the screenshot below.
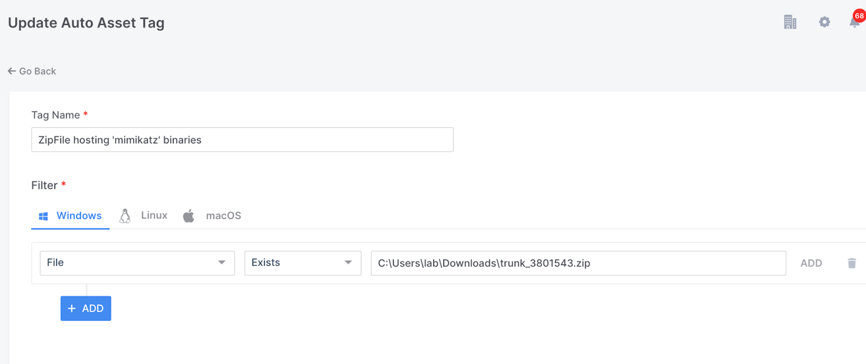
This simple query will tag any of our Windows endpoints where the downloads folder contains the file ‘trunk_3801543.zip’
Osquery in AutoAsset Tagging
As you may already know, AIR harnesses the power of Osquery as one of the options available in our Triage functionality. But, what is not so well known, is that you can use this amazingly granular and powerful capability in Auto Asset Tagging.
What this means is that you can leverage thousands of variables from almost every part of your endpoint’s systems and tag those identified assets as soon as the AIR agent is deployed, or at any stage later when you choose to re-run Auto Asset Tagging.
AIR provides two ways for constructing your query. You can use our built in Query Builder templates, which is a great option to make it simple and helps avoid many common syntax errors. Or, if you prefer you can use the Advanced editor which allows for the manual entry of queries or cut and paste operations.
Let's take a look at some examples.
The Windows prefetch file is often a good place for DFIR investigators to hunt for the activity of ‘bad actors’. In the event of a cyber-attack, the timeline of evidence captured in prefetch files can prove extremely useful in determining the root cause.
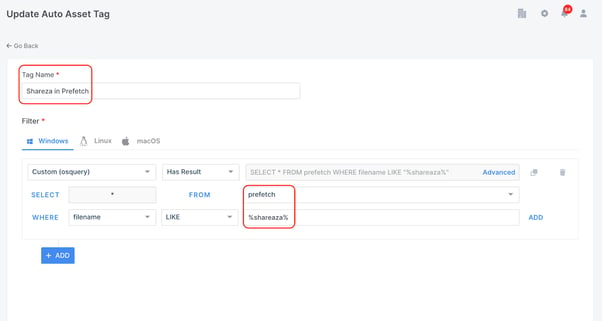
Evidence of program execution could be a valuable resource as it could prove that an attacker ran a program such as Shareaza to share illegal files. If the program has since been deleted, a prefetch file may still exist on the system to provide evidence of execution.
In the example below you can see that I have used the AIR Query Builder to generate an Auto Asset Tag which will automatically tag any machines with prefetch files that have filenames containing ‘Shareaza’.
In the next example below I am asking AIR to automatically tag any machines where this particular version of Shareaza exists as a program. This time I have used the Advanced option so I was able to cut and paste the query from my bank of queries.
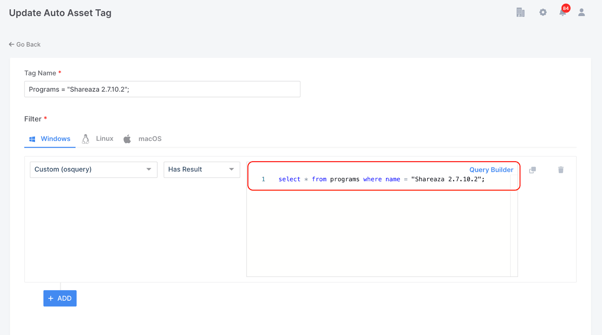
The final example below is another manually entered query which will tag any of my endpoints where the process "Shareaza.exe" exists.
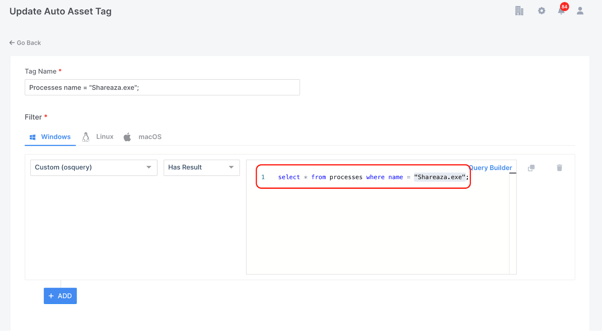
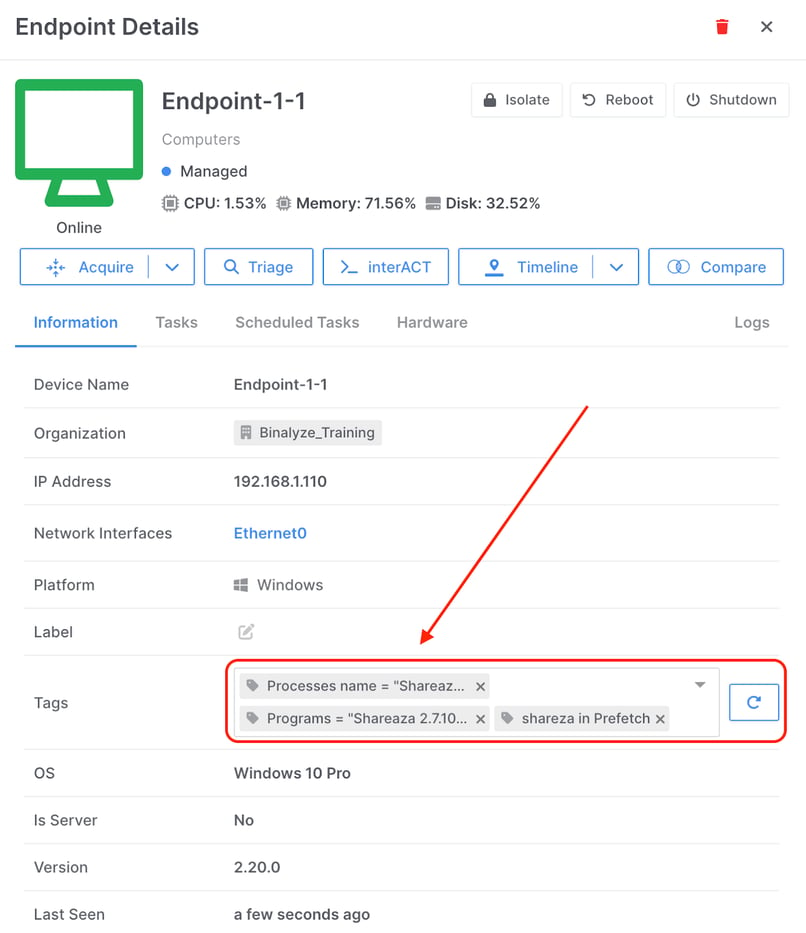
I could of course, merge all three of the queries discussed above into the one Auto Asset Tag, but for the purpose of this demonstration I wanted to show how when I re-run Auto Asset Tagging on a test machine where I have Shareaza installed, I will have generated tags for all three of the queries written.
Auditing of Auto Asset Tags
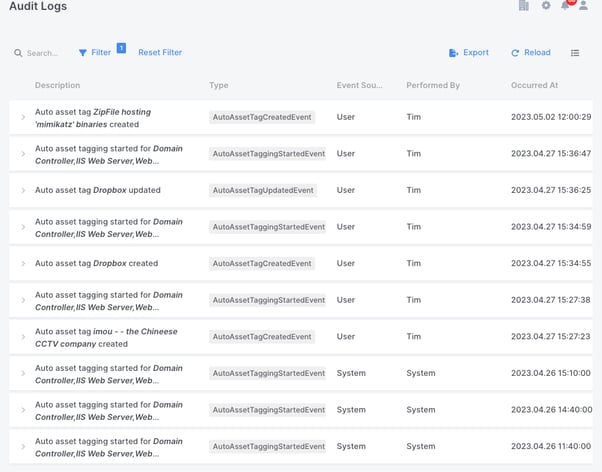
As with everything in AIR, all of this Auto Asset Tagging activity is thoroughly tracked in AIR’s audit logs and the audit logs can be filtered to reveal just Auto Asset Tagging activity, such as Tag Creation, Tag Updates and the actual running of the tagging event:
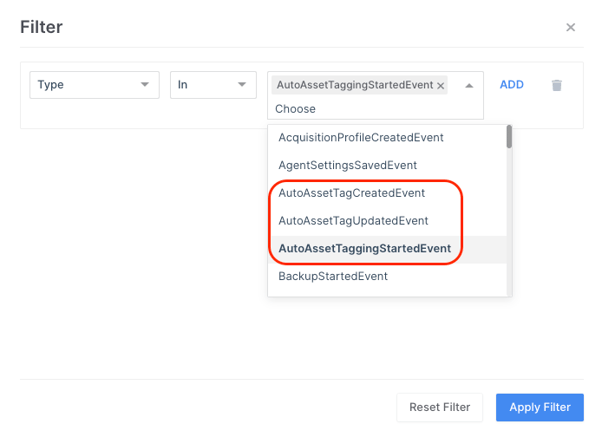
The screenshot of the audit logs below reveal the initial Auto Asset Tagging events on installation of the AIR agent by the system and then the subsequent User activity which generated the Auto Asset Tags as mentioned in this article.
The Tags generated by Auto Asset Tagging, as well as user generated tags, can be used to create Policies.
In the example below I have created a policy using tags for infected machines, so this policy will apply when there is a match with machines that have been tagged with either ‘Infected’ or ‘Infected Systems’ in the Binalyze EU organization.
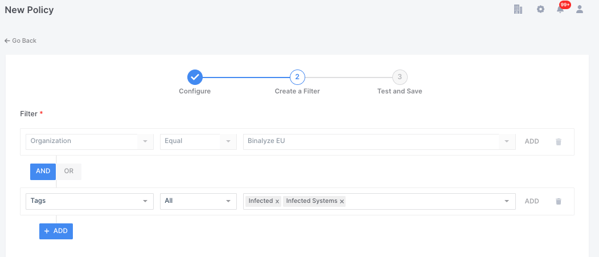
So, in this use case my policy could be used to save any data collected from a machine tagged as infected to a different evidence repository or to enforce a different password on the encrypted output.
Conclusion
Auto Asset Tagging will dramatically help you speed up the investigation process by giving you visibility across network assets in an automated and timely fashion. In addition, it opens up many other creative possibilities by using custom built Auto Asset Tags to look for very unique conditions and even the presence of individual files and artefacts that might well be indicators of compromise.
Auto Asset Tagging gets really effective when used in a proactive way. Consider scheduling regular evidence acquisitions or compromise assessments on your critical assets and use the findings identified by AIR automatically to generate new Auto Asset Tags. This will deliver a new level of cyber resilience to your network or customer.










