1 min read


Since efficiency and simplicity are at the core of Binalyze solutions, in this product release we incorporated the compression and encryption feature.
It is a very straightforward feature where its main purpose is to reduce network bandwidth, reduce file size to save disk capacity and encryption as its name says for increased security.
Here is how you can enable Compression & Encryption:
Go to your AIR Dashboard, choose any endpoint, and click on “Acquire”
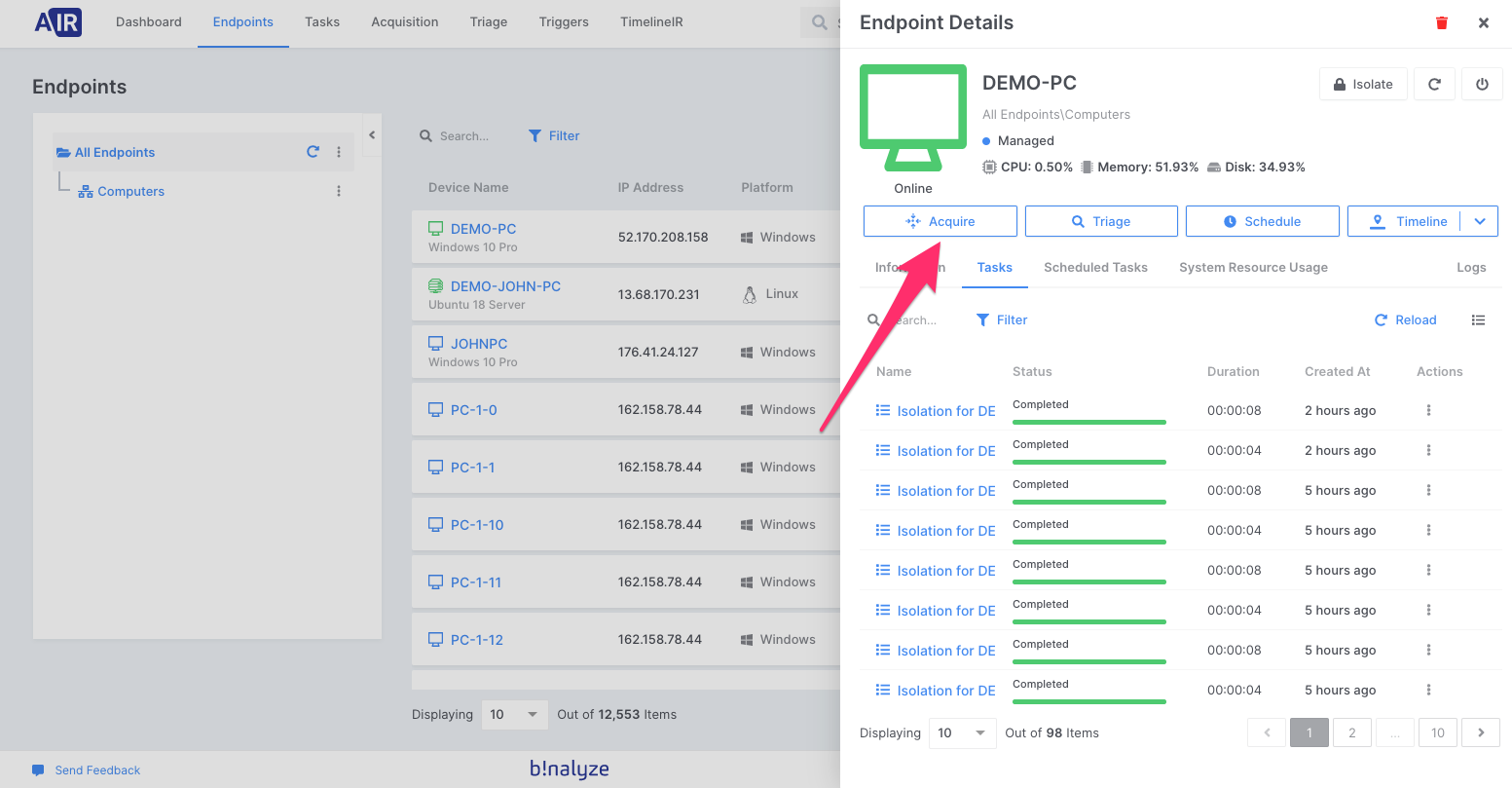
2. Under options select “Use custom options” and in the “Compression & Encryption” section click on “Configure”
.png?width=600&name=Acquire_Evidence_-_AIR___Binalyze%20(1).png)
3. Here you can enable the Compression and Encryption features separately as desired. Once you enable the Encryption module you will type a password that will be used to unlock the evidence files which are encrypted using AES 256.
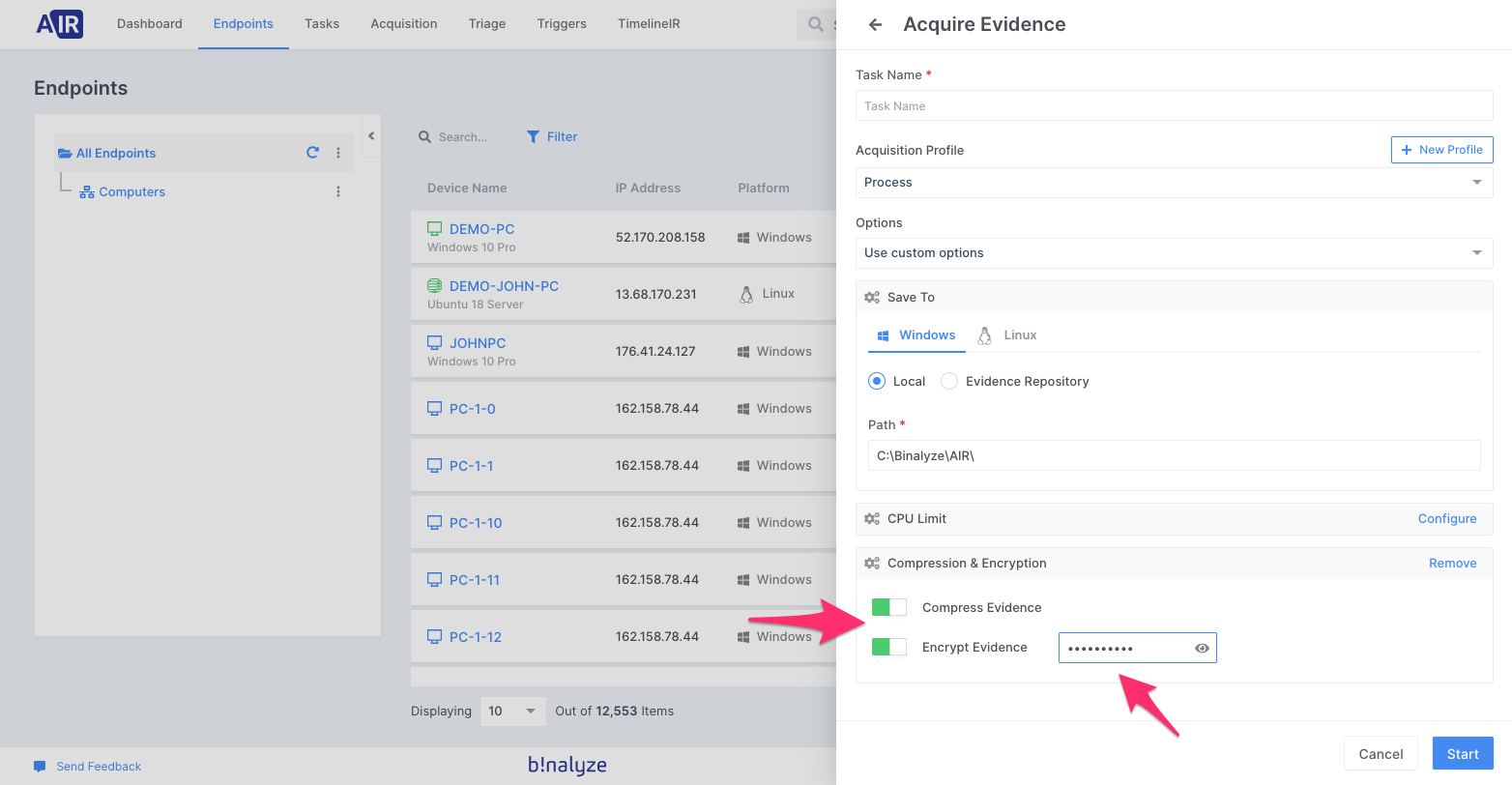
Now you are ready to go. Click on the start button and AIR Endpoint will start acquiring evidence. Once the evidence files are acquired, based on configurations that you have defined previously, files will be stored in the location you choose.
Watch a demo of Binalyze AIR 1.7.35 new product release where our founder Emre Tinaztepe demos the new feature highlights.
To download the update visit AIR product page..