.png)
Welcome to the AIR 4.11/4.10 release blog which introduces features and enhancements designed to streamline your forensic investigations and improve system functionality.
Highlights include the debut of Frank, an AI Assistant poised to revolutionize investigation processes within the AIR console by offering real-time forensic support and insights.
Additionally, we've again expanded our support for new evidence types to over 580 items across Windows, macOS, IBM AIX, and Linux. We have also introduced key enhancements like error reporting in disk imaging, task scheduling based on asset timezones for synchronized operations, and an improved Auto Asset Tagging wizard for organizational flexibility.
Thanks to some prompt feedback from some of our great customers, an important timestamp issue with the Event log content has been fixed.
Please read on for the details.
Features
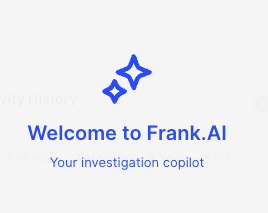
AIR 4.11 Introduces Frank.AI - Your Forensic Investigation Copilot
We're excited to unveil Frank.AI in our AIR 4.11 preview release. Frank is an AI Assistant designed to seamlessly integrate into your workflow, enhancing the forensic investigation process within the AIR console. Here's everything you need to know about Frank.AI and how it can transform your investigative work.
What Can Frank.AI Do for You?
Frank.AI is not just another tool; it's your investigation partner, available anytime, directly within the AIR console. Frank.AI aims to provide:
-
Direct Access: Instant availability across the AIR console for any inquiries, speeding up your investigations.
-
Instant Knowledge Support: Quick, AI-powered insights to bridge gaps in your forensic analysis, ensuring you're always prepared for the next step.
-
Enhanced Rule Creation: Simplified creation of YARA, Sigma, and Osquery rules, expanding your toolkit without the complexity.
As we launch Frank.AI, remember that this is just the beginning. Frank.AI will evolve, shaped by your feedback and the integration of advanced AI technologies, to offer even more nuanced assistance.
Frank.AI in AIR 4.11: Preview Version Highlight
In this initial rollout, Frank.AI leverages the ChatGPT API to assist with forensic-related questions, including advice on YARA, Sigma, and Osquery rules. While this version doesn't include fine-tuning or pre-training, it sets the groundwork for substantial future enhancements.
Upcoming Enhancement
-
Retrieval Augmented Generation (RAG): Future versions will see Frank.AI accessing a wider array of data sources for broader, more accurate responses.
-
Deeper AIR Ecosystem Integration: Frank.AI will eventually fetch data directly from the AIR database, integrating more deeply into the AIR framework for enhanced capabilities.
-
Advanced Analysis Features: Expect Frank.AI to offer anomaly detection and behavioral correlations by analyzing data through the AIR's AI module.
How to Interact with Frank.AI
To start a conversation with Frank, look for the Frank AI chat icon on any page within the AIR Console, positioned in the bottom left corner over the settings icon. Frank is ready to assist with digital forensics, incident response, or any aspect of your investigation.
Requirements and Security
Frank.AI is hosted on one.binalyze.com and available to all licensed AIR users. Developed with a focus on security, Frank.AI operates through a proxy server, ensuring that no customer data is sent to external services. Users are advised not to share confidential information within their messages and prompts.
The Road Ahead
Frank's journey is just beginning, with ambitious plans for expansion and enhancement based on your feedback and the evolving needs of digital forensic investigations. Our dedicated Confluence page will keep you updated on Frank's development and the exciting new features we have in store.
Conclusion
Frank.AI represents a significant leap forward in forensic investigations, providing AIR users with an intelligent, accessible assistant that simplifies complex processes and enhances investigative capabilities. As we continue to develop Frank.AI, we're excited to see how it will transform the way you approach forensic analysis and investigation within the AIR ecosystem.
Yet more evidence types are supported in 4.10/4.11
New Windows evidence types:
|
Category |
Name |
Collection Type |
|
Process Execution |
Parse LNK Files |
Parsed & presented in Investigation Hub |
|
Process Execution |
Collect LNK Files |
File collected |
-
New Linux evidence type:
|
System |
Systemctl Services |
Parsed & presented in Investigation Hub |
-
New Windows, macOS, and Linux evidence types:
|
Browser |
Chrome Sessions |
Parsed & presented in Investigation Hub |
|---|---|---|
|
Browser |
Chrome Login Data |
Parsed & presented in Investigation Hub |
|
Browser |
Chrome Local Storage |
Parsed & presented in Investigation Hub |
|
Browser |
Chrome IndexedDB |
Parsed & presented in Investigation Hub |
|
Browser |
Chrome Web Storage |
Parsed & presented in Investigation Hub |
|
Browser |
Chrome Form History |
Parsed & presented in Investigation Hub |
|
Browser |
Chrome Thumbnails |
Parsed & presented in Investigation Hub |
|
Browser |
Chrome Favicons |
Parsed & presented in Investigation Hub |
|
Browser |
Default Browser |
Parsed & presented in Investigation Hub |
|
Browser |
Firefox Cookies |
Parsed & presented in Investigation Hub |
-
Credit: Ashok K
-
A full list of the 584 items now supported in AIR is available in the Knowledge Base.
Enhancements
-
Binalyze MITRE ATT&CK Analyzer has been updated to version 4.3.0
-
-
In our relentless pursuit to bolster cybersecurity defenses against evolving threats, we're excited to announce yet more updates to our MITRE ATT&CK Analyzer in version 4.3.0. This release encompasses a wide array of enhancements, including new malware detection capabilities.
-
Here, we highlight some key updates and new detections:
-
Xdealer Malware Detection: One of the notable additions is the detection of Xdealer malware, linked to the China-nexus threat actor known as Earth Lusca (G1006). Xdealer has been a significant threat, particularly for its sophisticated mechanisms and the critical infrastructures it targets. By integrating detection capabilities for this malware, our analyzer empowers cybersecurity professionals to identify and mitigate threats posed by this actor more effectively.
-
DinodasRAT: The update also introduces detection for a custom malware dubbed DinodasRAT (G1006), which has been specifically designed to infiltrate government organizations. This addition underscores our tool's adaptability to emerging threats and its role in safeguarding sensitive governmental operations from targeted cyber espionage.
-
Lumma Information Stealer Insights: Another highlight is the enhanced detection of the Lumma information stealer (also known as LummaC2 Stealer), tagged under multiple techniques like T1082, T1622, and T1140, among others. Lumma's capabilities to stealthily exfiltrate valuable information make it a significant threat. Our analyzer's updated detection mechanisms provide an essential layer of defense, identifying and addressing the diverse tactics employed by this stealer.
-
In addition to malware detections, our Dynamo update introduces an expanded Hacker Tool list with new keywords for hunting in forensic artifacts. This enhancement is crucial for a deeper, more comprehensive analysis across various system artifacts like Applications, Cronjobs, and MFT, tagged under T1588.002. Such advancements in artifact analysis are instrumental in uncovering subtle indicators of compromise, fortifying defenses against sophisticated threat actors.
-
For a detailed overview of all the updates and improvements in version 4.3.0 of the MITRE ATT&CK Analyzer, we encourage our users to visit our knowledge base. Together, let's strengthen our cyber defenses and protect our digital ecosystems against the threats of tomorrow.
-
-
-
Disk imaging errors reported in metadata.yml
-
AIR’s disk or volume imaging feature produces a file that captures the metadata related to the imaging process. This now includes a log of any errors encountered, which are documented within the metadata.yml file for comprehensive tracking and analysis. (Credit: Charlotte H)
-
Please see this KB article for a full explanation.
-
-
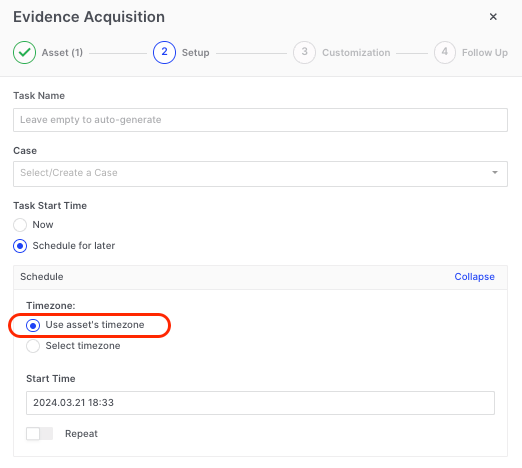
Scheduling Based on Asset Timezone
-
AIR now enables users to schedule tasks according to the asset's local time zone. This ensures that tasks are executed at the specified time relative to each asset's geographical location, allowing for synchronized operations across different time zones. For example, when choosing this option, instructing the system to perform a task at 01:00 will result in the task being carried out at 01:00 in the local time of each asset, regardless of their global positions. (Credit: Ramesh P)
-
Please see this KB article for more information.
-
-
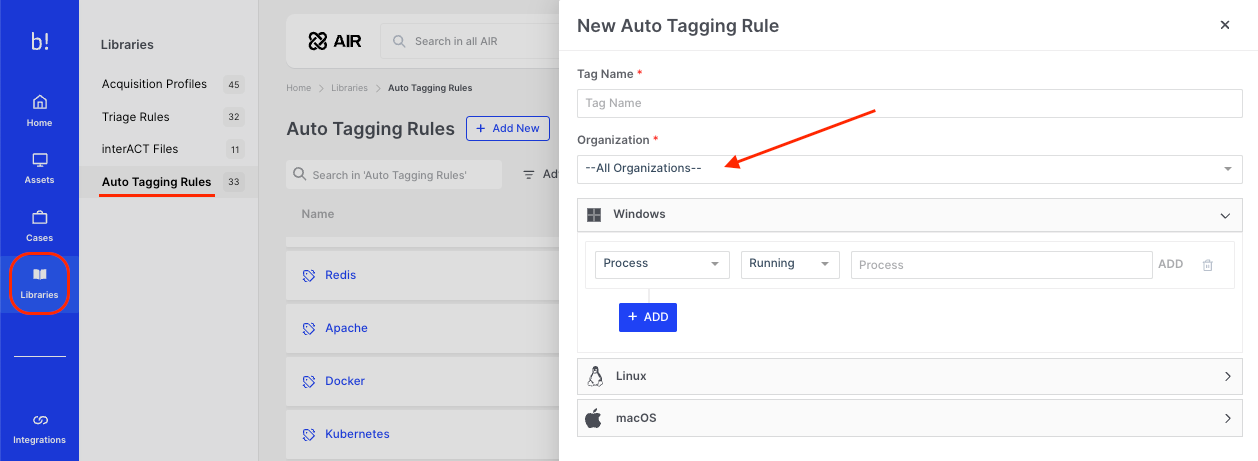
Auto Asset Tagging Rules: New wizard and Organizational Saving
-
The new Auto Asset Tagging (AAT) wizard allows rules to be saved specifically for individual organizations or universally across all organizations. This enhancement supports users in creating and applying incident-specific AATs selectively, avoiding unnecessary use or exposure of a rule outside the intended organizational context. (Credit: Caleb T)
-
Please read this Auto Asset Tagging KB page for more information.
-
-
AIR version information is again displayed in the main menu
-
The AIR console version number has returned to the main menu to stop users from having to locate it on the settings page.
-
Fixes
-
A timestamp issue with the Event log content has been fixed. (Credit: Jon F, Grant O and Ben H)
-
Some incorrect "Match Counts" under the "Case Triages" Page have been resolved.
-
In previous versions, AIR displayed the "KeyLastWriteTime" in the evidential Amcache CSV files in local time instead of UTC. This has now been corrected to show times in UTC, ensuring consistency and accuracy. (Credit: Guo Y)
-
Tornado, crucial for AIR's File Explorer integration, retries registration until successful. A bug affecting success confirmation was fixed, enhancing reliability. (Credit: Nuno P)









